Guest article contribution by Joann Needleman and Ann Lemmo of Clark Hill Law.
Cash may be king, but credit is power. More people are relying on credit cards as their main source of payment. Businesses have responded by making credit card payments easier and more accessible, including in paying off debt. However, the reliance on credit cards has also made credit card information easier and more accessible to hackers.
That being said, companies must ensure that cardholder information is properly protected. For this reason, the leading credit card brands American Express, Discover Financial Services, JCB, MasterCard, and Visa, Inc. created the Payment Card Industry (PCI) Security Standards Council which regulates the PCI Data Security Standard (PCI DSS). However, for any entity that accepts credit cards, meeting these standards is onerous, time consuming, and expensive.
Sensitive PCI Card Data

What’s Required for PCI Compliance?
PCI DSS has 12 requirements:
- Install and maintain a firewall configuration to protect cardholder data;
- Change vendor-supplied defaults for system passwords;
- Protect stored cardholder data;
- Encrypt transmission of cardholder data across public networks;
- Protect all systems from malware and regularly update anti-virus software or programs;
- Develop and maintain secure systems and applications;
- Restrict access to cardholder data by limiting its use to business need-to-know;
- Identify and authenticate access to system components;
- Restrict physical access to cardholder data;
- Track and monitor all access to network resources and cardholder data;
- Regularly test security systems and processes; and
- Maintain a policy that addresses information security for all personnel.
Card Brands May Have Different PCI Compliance Requirements
While PCI DSS is considered the “global standard,” each card brand may have its own program for compliance, validation levels, and enforcement. Not only may the companies require different security measures, but they also require different reporting methods. For example, individual card brands validate compliance by either external Qualified Security Assessor or by a firm-specific Internal Security Assessor that creates a report on compliance or by Self-Assessment Questionnaires.
State Requirements for PCI Compliance
Card brand requirements aren’t all a business needs to consider. Each state also may have different requirements or even require you to meet PCI DSS by state law. For example, in 2007, Minnesota signed into law the Plastic Card Security Act (“PCSA”), set out in Minnesota Statutes § 325E.64. In 2009, Nevada incorporated the standard into law. It specifically required compliance with PCI DSS and provided a shield for compliant entities from liability. See Nev. Rev. Stat. § 603A.215.
Finally, in 2010, the state of Washington made it so that entities were not required to be compliant with PCI DSS, but those that were are shielded from liability. See 2010 Wash. Sess. Laws 1055 § 3. Thus, while for the most part PCI compliance is self-regulated by the card brands, states have gotten on board to make it law.
The Cost of PCI Requirements
Compliance can be cost-prohibitive. There are constant software upgrades, network checks, personal firewalls, employee monitoring as well as annual auditing and reporting. In the event of non-compliance, access to devices could be restricted. Thus, any entity that wishes to provide credit card payment options will need to invest in not only compliant equipment, but also develop monitoring methods, training programs, and a competent team that can manage the different reporting requirements for not only each card brand but for each state where applicable.
Why Outsource PCI?
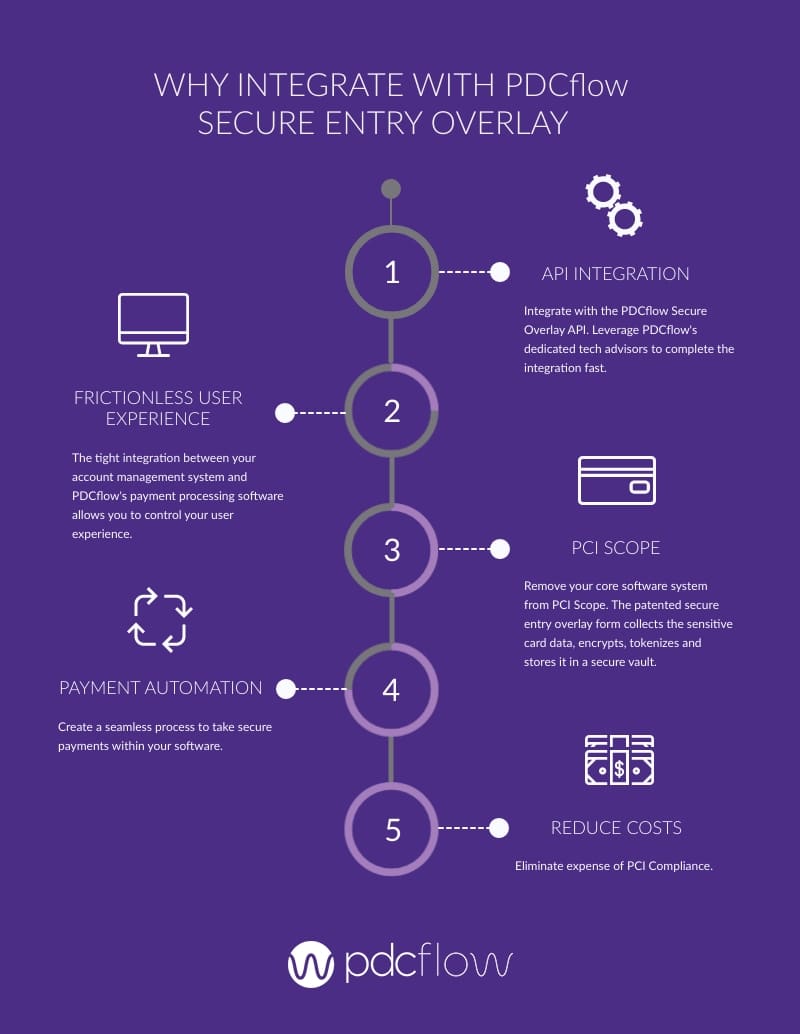
Outsourcing PCI responsibilities is an alternative. Consider a payment processing system that integrates with your current software in order to take it out of the PCI scope. This works by providing a secure overlay on top of your current software platform allowing your customers to work within your current software platform with no disruption.
Customers provide their credit card information directly onto your platform but the credit card fields are actually hosted on a separate PCI certified server, usually in a remote location. The outside host server receives the credit card number directly, tokenizes it, and returns the token to the current software platform. The tokenization replaces the credit card number with a randomly generated code. The code has no value to hackers because it is not the actual credit card number.
This process allows an entity to utilize all the standard credit card functions, like processing voids, credits, or recurring payments in real time or even at a future date without actually having the card number. Further, these payment processing systems minimize your headache of PCI compliance requirements while still offering your customers the necessary payment flexibility and security.
Credit cards are an unavoidable method of payment. Don’t let PCI deter you from offering your customers fast, safe and easy payment methods; leave data security to the data security experts.
Outsource your PCI responsibilities with a PDCflow integration:
- Reduce PCI compliance cost and efforts
- Protect consumer card data from a data breach
- Build trust with consumers with a secure system for collecting sensitive information
Download our Secure Entry Overlay document and learn more about PDCflow's patented technology.